sslTunnel document
sslTunnel is free software used to secure traffic running between a TCP client and server. It is designed to work as an SSL encryption wrapper, encrypting the messages using TLS/SSL and allowing for secure communication without changing the program running on either side of the TCP connection.
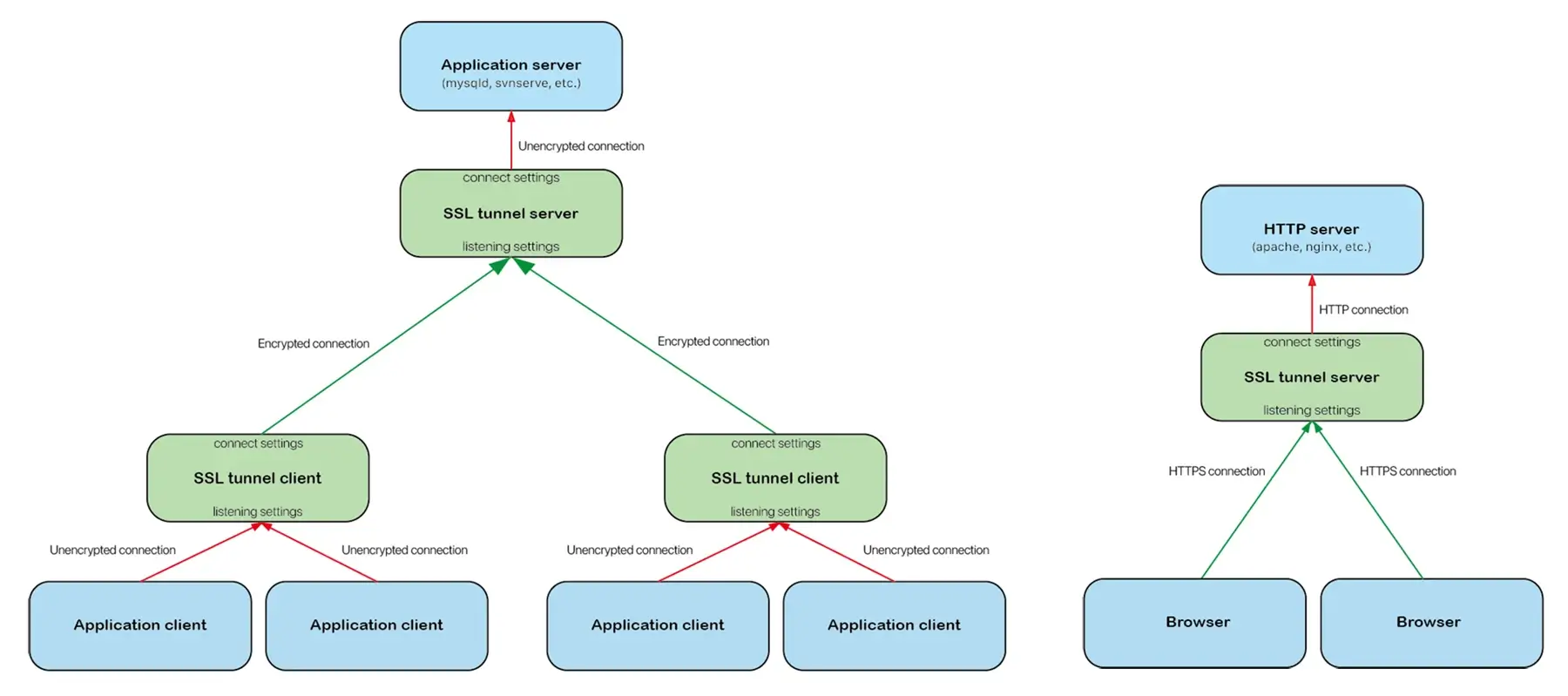
Installation
Debian, Ubuntu
Download the appropriate
.debpackage from our download page, then install it:sudo dpkg -i ssltunnel-linux-XXXX.deb
Edit the configuration file
/etc/ssltunnel/config.json, define your tunnels in it.Start the
ssltunnelservice.sudo systemctl start ssltunnel.service
CentOS,Rocky,AlmaLinux,Oracle linux, Springdale, Fedora,RedHat
Download the appropriate
.rpmpackage from our download page, then install it:sudo yum install ssltunnel-linux-XXXX.rpm # or 'sudo dnf install ssltunnel-linux-XXXX.rpm'
Edit the configuration file
/etc/ssltunnel/config.json, define your tunnels in it.Start the
ssltunnelservice.sudo systemctl start ssltunnel.service
macOS, Windows, FreeBSD, OpenBSD, NetBSD, DragonFly, other Linux
Download the appropriate
.zippackage from our download page, then decompress it.Optionally, create a user to run the
ssltunnel.Create a configuration file
ssltunnel.json, define your tunnels in it.Start the
ssltunnel:sudo ssltunnel --config=ssltunnel.json
Command line
Usage
ssltunnel [--config=<CONFIG_FILE>] [--mono] [--foreground] [--show-pid] # Run as daemon service.
ssltunnel --showcfg [--config=<CONFIG_FILE>] [--passphrase] [--mono] # Display current configuration.
ssltunnel --version [--mono] # Display version information.
ssltunnel --help # Display the usage.Options
--config=<CONFIG_FILE>: Specifies the configuration file. If not specified, the following files are used in order.The
ssltunnel.jsonfile in the directory where the ssltunnel command is located.The
~/ssltunnel.jsonfile in the current user's home directory.The
/etc/ssltunnel/config.jsonfile (except Window).
--foreground: Runs the ssltunnel in the foreground using the current user and group, without forking a new process. By default, the ssltunnel will read the configuration file and then fork a new process using the user and group specified in the configuration, then terminate the current process.--show-pid: Display the process ID. If the--foregroundisn't specified, the process ID of the forked new process will be displayed.--mono: Disable to colorize the output.--showcfg: Show current configuration.--passphrase: Specifies to display the pass phrase for the certificate private key when displaying the configuration.--help: Display help information about ssltunnel.--version: Display version information.
Configuration file
# sslTunnel configuration file. # The user who starts ssltunnel must have read permissions to the file. The user set below to run # ssltunnel does not need any permissions on this file. Usually use the root user to start the # ssltunnel, so set the owner and group of the configuration file to the root user, and set its # permissions to 400. { # Specifies a user to run the service as. If the --foreground option isn't specified, ssltunnel # will fork a new process with the user after running, and then terminate the current process. # The user does not need to have any permissions on this configuration file, certificate files, # and certificate private key files. "user": "ssltunnel", # Specifies a group to run the service as. If the --foreground option isn't specified, ssltunnel # will fork a new process with the group after running, and then terminate the current process. "group": "ssltunnel", # The tunnel definitions "tunnels": [ # First tunnel definition { # Listening settings: # - When used as a ssl tunnel server: Listen for ssl tunnel client connections. # - When used as a ssl tunnel client: Listen for connections from downstream application # clients. "listen": { # Tunnel listening address (supports both IPv4 and IPv6 address, blank indicates # all IPv4 and IPv6 addresses. The square brackets are not needed for IPv6). "address": "127.0.0.1", # Tunnel listening port. "port": 4120, # Server certificates. # - When used as a ssl tunnel server: Specifies the server certificates in order to # listen for encrypted incoming connection from ssltunnel client. If multiple # domain names are allowed to be used to connect to the server, a certificate # needs to be specified for each domain name (general domain name certificates and # multiple domain names certificates can also be used). # - When used as a ssl tunnel client: Don't specify the server certificates in order # to listen for unencrypted incoming connections from application clients. The # remaining listening settings ("client-auth", "client-verify", "ca", and "custom") # will be ignored. "certs": [ # First certificate. { # The path to the certificate file, or the path to the full certificate # chain file (if it is a relative path, it is based on the directory where # the configuration file is located). The user who starts ssltunnel must # have read permissions to the file. The user set above to run ssltunnel # does not need any permissions on this file. "cert": "...", # The private key file path (if it is a relative path, it is based on the # directory where the configuration file is located). The user who starts # ssltunnel must have read permissions to the file. The user set above to # run ssltunnel does not need any permissions on this file. Usually use the # root user to start the ssltunnel, so set the owner and group of the # certificate private key file to the root user, and set its permissions to # 400. "key": "...", # Specifies the pass phrase if the private key is encrypted,otherwise the # user will be prompted for a pass phrase on starting the ssltunnel. "passphrase": "..." }, # Other certificates. ... ], # Determines the server's policy for TLS client authentication. # - no: Indicates that no client certificate should be requested during the # handshake, and if any certificates are sent they will not be verified. # - request: Indicates that a client certificate should be requested during the # handshake, but does not require that the client send any certificates. # - any: Indicates that a client certificate should be requested during the # handshake, and that at least one certificate is required to be sent # by the client, but that certificate is not required to be valid. # - optional: Indicates that a client certificate should be requested during the # handshake, but does not require that the client sends a certificate. # If the client does send a certificate it is required to be valid. # - verify: Indicates that a client certificate should be requested during the # handshake, and that at least one valid certificate is required to be # sent by the client. "client-auth": "verify", # Determines how the server verifies client certificates: # - cert: Only verify the end-entity (leaf) client certificate against a certificate # specified in "ca" below. # - ca: Verify the client certificate chain starting from the root CA. "client-verify": "ca", # Certificate Authority files, specifies one or multiple certificates, to be used # to verify client certificates. If a relative path is used, it is based on the # directory where the configuration file is located. It's required if "client-auth" # above is set to "optional" or "verify". The user who starts ssltunnel must have # read permissions to these files. The user set above to run ssltunnel does not need # any permissions on these files. # - When "client-verify" above is set to "cert": Specifies all end-entity (leaf) # client certificates here. Multiple certificate files can be specified, each file # can contain multiple end-entity (leaf) client certificates. # - When "client-verify" above is set to "ca": Specifies the issuing certificate # chain starting with the root CA certificate for all client certificates. # Multiple certificate chain files can be specified. "ca": [ # First certificate file or certificate chain file. "...", # Other certificate file or certificate chain file. ... ], # Custom configuration. See Customized configuration. "custom": "..." }, # Connection settings: # - When used as a ssl tunnel server: Connect to the upstream application server. # - When used as a ssl tunnel client: Connect to the ssl tunnel server. "connect": { # Destination address for connection. It can be an IP address (both IPv4 and IPv6 # are supported, and the square brackets are not needed for IPv6.) or a domain name. # If the connection destination is TLS/SSL server, the domain name generally needs # to be specified here, otherwise a domain name needs to be specified in the # "server-name" below so that the server provides an appropriate certificate. "address": "domain.com", # Destination port for connection. "port": 3690, # Connection timeout (seconds), its default value is 10 seconds. "timeout": 10, # Specifies whether the connected server is an TLS/SSL encryption server. If it is # set to false, the remaining connect settings ("server-name", "certs", "server-verify", # "ca", and "custom") will be ignored. # - When used as a ssl tunnel server: Set to false in order to connect to the upstream # application server. # - When used as a ssl tunnel client: Set to true in order to connect to the ssl tunnel # server. "tls": true, # Specifies the server name indication extension sent by the client. the value of # "address" above will be used if it isn't set. It's required if the "address" is set # to a IP address, and it must match least one server certificate. "server-name": "domain.com", # Specify the client certificate if the server needs to verify the client # certificate. "certs": [ # First certificate. { # The path to the certificate file, or the path to the full certificate # chain file (if it is a relative path, it is based on the directory where # the configuration file is located). The user who starts ssltunnel must # have read permissions to the file. The user set above to run ssltunnel # does not need any permissions on this file. "cert": "...", # The private key file path (if it is a relative path, it is based on the # directory where the configuration file is located). The user who starts # ssltunnel must have read permissions to the file. The user set above to # run ssltunnel does not need any permissions on this file. Usually use the # root user to start the ssltunnel, so set the owner and group of the # certificate private key file to the root user, and set its permissions to # 400. "key": "...", # Specifies the pass phrase if the private key is encrypted,otherwise the # user will be prompted for a pass phrase on starting the ssltunnel. "passphrase": "..." }, # Other certificates. ... ], # Determines how the client verifies server certificate: # - skip: Don't verify the server certificate, the setting "ca" below will be ignored. # - cert: Only verify the end-entity (leaf) server certificate against a certificate # specified in "ca" below. # - ca: Verify the server certificate chain starting from the root CA. "server-verify": "ca", # Certificate Authority files, specifies one or multiple certificates, to be used # to verify server certificate. If a relative path is used, it is based on the # directory where the configuration file is located. It's required if "server-verify" # above is set to "cert" or "ca". The user who starts ssltunnel must have # read permissions to these files. The user set above to run ssltunnel does not need # any permissions on these files. # - When "server-verify" above is set to "cert": Specifies the end-entity (leaf) # server certificate here. # - When "server-verify" above is set to "ca": Specifies the issuing certificate # chain starting with the root CA certificate for the server certificate. "ca": [ # First certificate file or certificate chain file. "...", # Other certificate file or certificate chain file. ... ], # Custom configuration. See Customized configuration. "custom": "..." } }, # Other tunnel definitions ... ] }
Custom configuration
In the configuration file, you can optionally specify custom configurations for each tunnel's listening settings and connection settings separately. The custom configuration value is a string that can contain multiple setting items separated by semicolons. Each setting item includes a name and a value separated by colons. For example:
"custom": "MinVersion: tls1.2; CipherSuites: RSA-RC4_128_SHA,ECDHE_RSA-RC4_128_SHA; CurvePreferences: P256; SessionTicketsDisabled: true"
Available setting items include:
MinVersion: Minimum TLS version that is acceptable. Available values include:tls1.0tls1.1tls1.2tls1.3ssl3.0
MaxVersion: Maximum TLS version that is acceptable. Available values include:tls1.0tls1.1tls1.2tls1.3ssl3.0
NextProtos: A list of supported application level protocols, in order of preference. If both peers support ALPN, the selected protocol will be one from this list, and the connection will fail if there is no mutually supported protocol. If it isn't specified or the peer doesn't support ALPN, the connection will succeed.CipherSuites: A list of enabled TLS 1.0–1.2 cipher suites separated by commas (Note that TLS 1.3 ciphersuites are not configurable). The order of the list is ignored. If not specified, a safe default list is used. Available items include:RSA-RC4_128_SHARSA-3DES_EDE_CBC_SHARSA-AES_128_CBC_SHARSA-AES_256_CBC_SHARSA-AES_128_CBC_SHA256RSA-AES_128_GCM_SHA256RSA-AES_256_GCM_SHA384ECDHE_ECDSA-RC4_128_SHAECDHE_ECDSA-AES_128_CBC_SHAECDHE_ECDSA-AES_256_CBC_SHAECDHE_RSA-RC4_128_SHAECDHE_RSA-3DES_EDE_CBC_SHAECDHE_RSA-AES_128_CBC_SHAECDHE_RSA-AES_256_CBC_SHAECDHE_ECDSA-AES_128_CBC_SHA256ECDHE_RSA-AES_128_CBC_SHA256ECDHE_RSA-AES_128_GCM_SHA256ECDHE_ECDSA-AES_128_GCM_SHA256ECDHE_RSA-AES_256_GCM_SHA384ECDHE_ECDSA-AES_256_GCM_SHA384ECDHE_RSA-CHACHA20_POLY1305_SHA256ECDHE_ECDSA-CHACHA20_POLY1305_SHA256
CurvePreferences: Specifies the elliptic curves that will be used in an ECDHE handshake, in preference order, separated by commas. If not specified, the default will be used. The connect settings will use the first preference as the type for its key share in TLS 1.3. Available item include:P256P384P521X25519
DynamicRecordSizingDisabled: Specifies whether to disable adaptive sizing of TLS records. Available values includetrueandfalse. Whentrue, the largest possible TLS record size is always used. Whenfalse, the size of TLS records may be adjusted in an attempt to improve latency.SessionTicketsDisabled: Specifies whether to disable session ticket and PSK (resumption) support. Available values includetrueandfalse. It may be set to true to disable session ticket and PSK (resumption) support. Note that this setting item is only valid in the listening setting.


 简体中文
简体中文
